Research Projects
Publications
- Meet Udeshi, Prashanth Krishnamurthy, Hammond Pearce, Ramesh Karri, and Farshad Khorrami. REMaQE: Reverse Engineering Math Equations from Executables. 2024. ACM Transactions on Cyber-Physical Systems. [doi] [pdf].
- Minghao Shao*, Sofija Jancheska*, Meet Udeshi*, Brendan Dolan-Gavitt*, Haoran Xi, Kimberly Milner, Boyuan Chen, Max Yin, Siddharth Garg, Prashanth Krishnamurthy, Farshad Khorrami, Ramesh Karri, Muhammad Shafique. NYU CTF Bench: A Scalable Open-Source Benchmark Dataset for Evaluating LLMs in Offensive Security. 2024. Neural Information Processing Systems (NeurIPS). [openreview] [pdf], [poster].
- Talor Abramovich, Meet Udeshi*, Minghao Shao*, Kilian Lieret, Haoran Xi, Kimberly Milner, Sofija Jancheska, John Yang, Carlos E. Jimenez, Farshad Khorrami, Prashanth Krishnamurthy, Brendan Dolan-Gavitt, Muhammad Shafique, Karthik Narasimhan, Ramesh Karri, Ofir Press. EnIGMA: Enhanced Interactive Generative Model Agent for CTF Challenges. 2024. (preprint, under review at USENIX). [arxiv].
- Meet Udeshi, Prashanth Krishnamurthy, Ramesh Karri and Farshad Khorrami. Tamper-Proof Network Traffic Measurements on a NIC for Intrusion Detection. 2024. IEEE Transactions on Network and Service Management, [doi].
- Nirmal Kumar Boran, Shubhankit Rathore, Meet Udeshi and Virendra Singh, Fine-Grained Scheduling in Heterogeneous-ISA Architectures. 2020. IEEE Computer Architecture Letters. [doi].
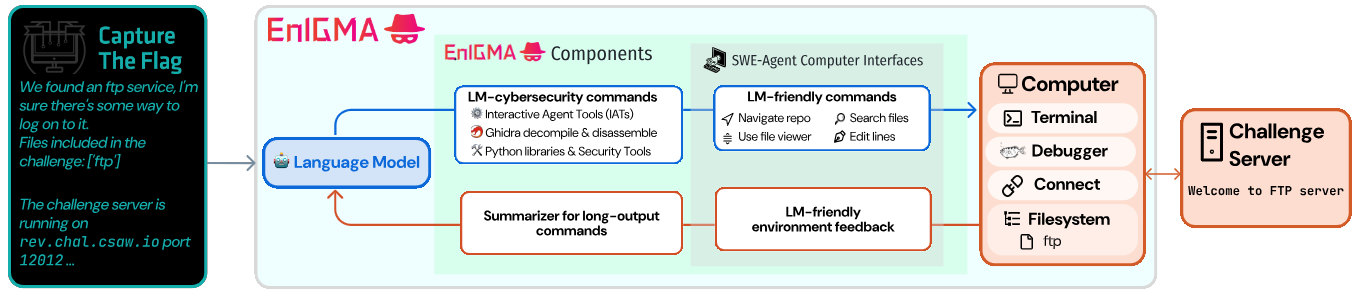
Developing LLM cybersecurity capabilities is important as LLMs are very useful in automating cybersecurity analysis with their vast breadth of knowledge. I worked on building the NYU CTF Bench dataset of CTF challenges to test LLM cybersecurity capabilities. I also worked on the EnIGMA agent with interactive agent tools and enhanced agent-computer interface.
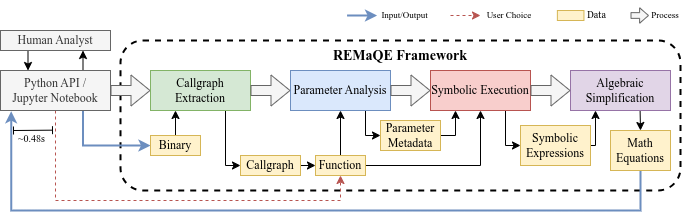
Reverse engineering math equations from binaries of embedded systems is immensely useful to analyze the implemented mathematical models for security purposes. I have developed two frameworks for reverse engineering math equations: REMaQE, an automated dynamic analysis framework utilizing symbolic execution; and REMEND, a neural decompilation framework with enhanced disassembler for extracting math equations using single pass static analysis.
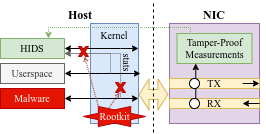
I have developed a framework that leverages the network interface card (NIC) to collect tamper-proof network traffic measurements for intrusion detection systems. Rootkits that compromise the host OS can tamper host-side network measurements but cannot easily touch peripherals that operate outside the host OS domain, such as the NIC. The framework can collect reliably accurate measurements with negligible impact to network performance.
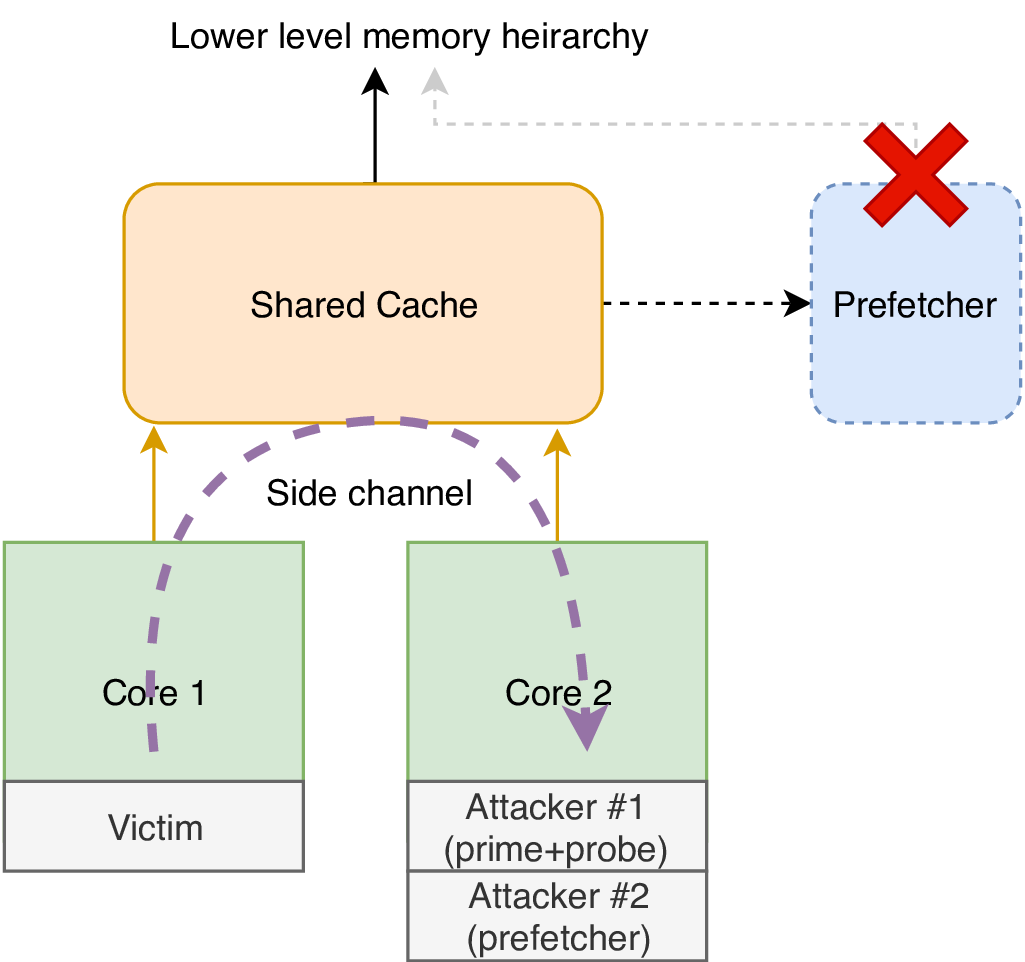
Cache side channels are well known for being effective in extracting data from modern cryptographic ciphers. Some other hardware accessing the cache, e.g. prefetcher, degrades the quality of the side channel by introducing false positives in the attacker’s data. This project works on a method to disable the prefetcher by preventing it from generating memory accesses and interfering with side channels running in the cache.
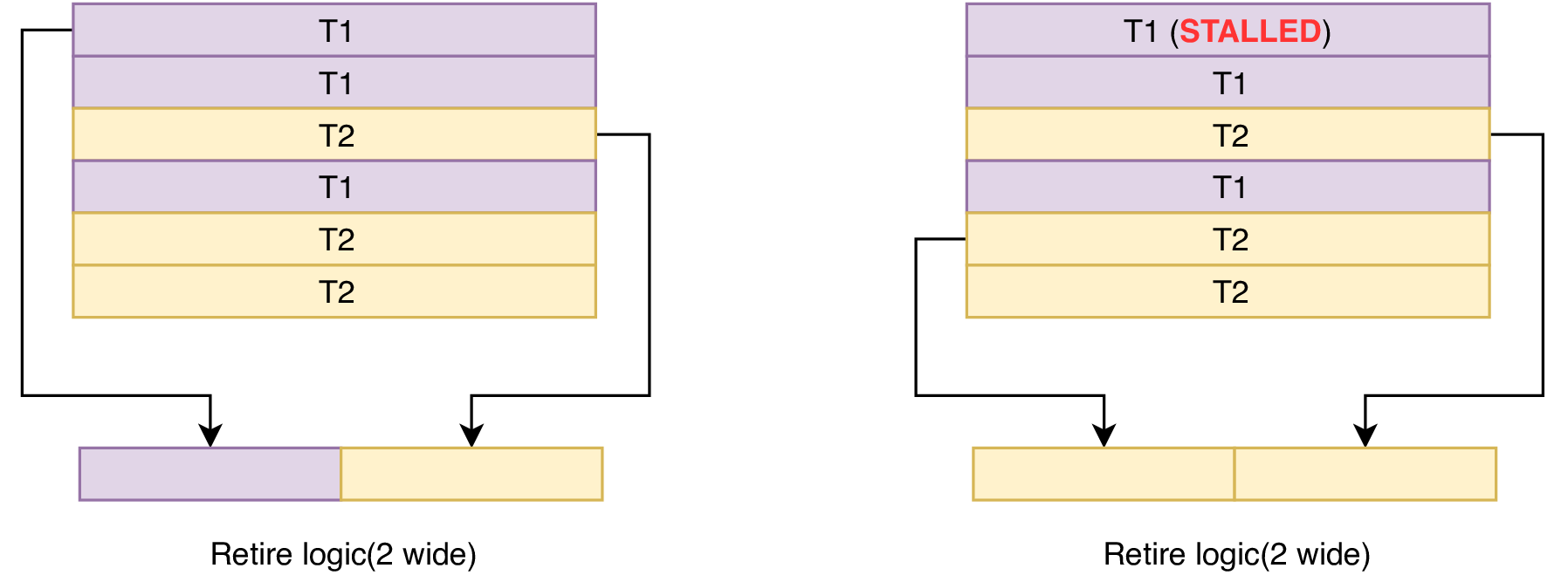
Reorder buffer is an important component of an Out-of-Order core utilised in the Tomasulo algorithm. In an SMT context, this Reorder Buffer may either be shared among threads or statically partitioned. This allows for a side-channel leakage to occur because a shared Reorder Buffer will lead to interference among the two thread’s IPC.
Heterogeneous-ISA Dynamic Core is a reconfigurable composite core which supports runtime migration between multiple ISAs. Runtime migration needs to ensure the consistency of memory image for both ISAs. This project implements a methodology for Exection Migration of HIDC between x86 and ARM ISAs. To harness the benefits of ISA diversity fully, execution migration cost needs to be low enough so that frequent migration can be justified performance-wise.